Statistics-based attacks are characterized by excessive packet arrival rate. The objective of the attacker is to send unfulfillable requests to a host at such an extreme rate that the host becomes overwhelmed, so can no longer fulfill genuine requests - the classic Denial of Service or DoS attack (from a single spoofed [non-existent] source IP address) or Distributed DoS attack (from multiple source addresses which may be spoofed).
Firewall DoS attacks target the firewall's session table, which is what the firewall uses to set up, manage and clear down sessions between sources (like your PC's email client) and hosts (like your email server). The attacker sends connection requests at an extreme rate, way beyond that which typifies normal user behaviour.
When the session table is full, the firewall cannot create any new sessions, so begins rejecting any new connection requests, including those from legitimate sources. The firewall's defence is to limit what constitutes an acceptable connection rate, beyond which packets containing connection requests are dropped.
For a more specific example, SYN-ACK-ACK proxy attacks target the three-way handshake used to establish TCP sessions - TCP is used, for example, in web browsing, email and file transfer. Under normal circumstances, the host sends an SYN segment to request session initiation with a host, the firewall intercepts it, creates an entry in its session table and proxies an SYN-ACK to the source, which replies with an ACK.
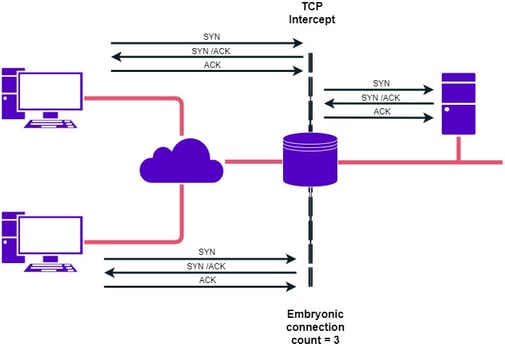
The user can then proceed with whatever it is they want to do. In the case of an attack, instead of replying with an ACK, a malicious source sends another ACK. Doing this repeatedly and at an extreme rate fills up the firewall's session table. The firewall's defence, in this case, is to limit the number of connection requests received from the same address, rejecting any further requests when the limit is reached.
These types of attack are also known as flood attacks, with specific attacks associated with different protocols, including ICMP (used most commonly for echo requests) and UDP (used for example by VoIP).
Land attacks combine an SYN attack (as described above) with the trick of specifying the host's IP address as the source and destination address in the attack packets.
This causes the target to send SYN-ACK packets to itself, creating empty connections which eventually time out. The firewall's defence is to inspect packet headers for this tell-tale addressing feature, combined with imposing a packet arrival rate threshold.
You might think that setting up statistics-based attacks requires considerable ingenuity on the part of the attacker, but it doesn't - tools for doing this are freely available and can be used by anyone capable of typing the target's IP address into an online form.
Happily, for Intercity's Touch Secure customers, every protection against all known statistics-based attacks is in place already, with new protections added literally every day. For those who can't quite see the point of putting leading-edge cybersecurity measures in place, perhaps the above will help explain what they do.
[subscribe-form]
Subscribe to our newsletter
YOU MAY ALSO BE INTERESTED IN:


